Passive Reconnaissance
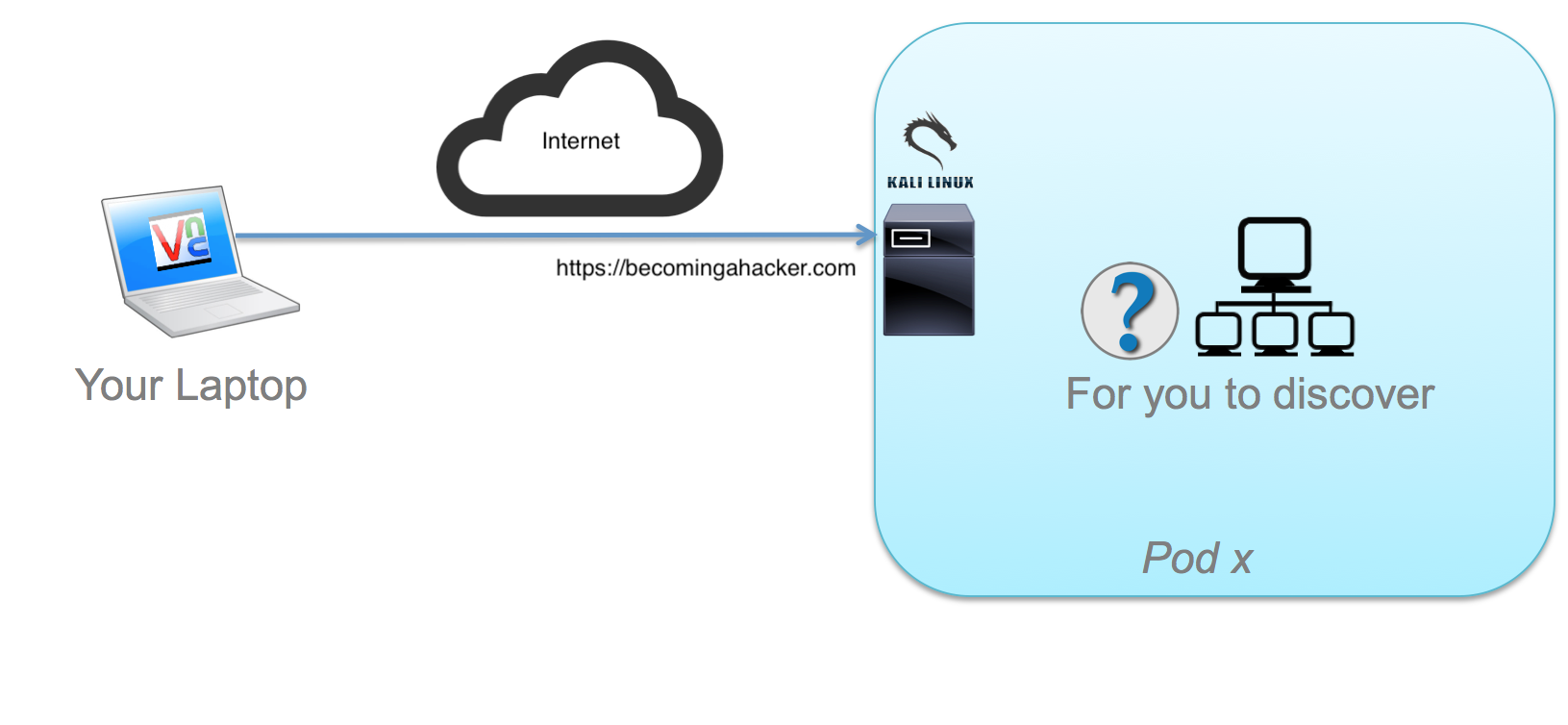
Kali Username: cisco Password: cisco
If you are sharing a pod, remember that there is only 1 graphical (VNC) session per pod, but there are 2 serial console ports you can use to keep your CLI work separate.
Intro: SecretCorp
Omar Santos owns secretcorp.org and this is not a real company. However, you will use it to practice your skills.
Exercise 1
In this exercise, we’ll use theHarvester to passively gather information about secretcorp.org.
theHarvester is a simple to use, yet powerful tool designed to be used during the reconnaissance stage of a red team assessment or penetration test. It performs open source intelligence (OSINT) gathering to help determine a domain’s external threat landscape. The tool gathers names, emails, IPs, subdomains, and URLs by using multiple public resources.
- You can see a list of options with
theHarvester --help. Since we’re interested in secretcorp.org, we’ll need to use the -d/--domain option.
- Try running
theHarvester --domain secretcorp.org. Do you see any results?
- Probably not, because you didn’t specify a
--source!
There are a lot of free OSINT resources available online. theHarvester doesn’t really do anything by itself– it just reaches out to these OSINT services and gathers information for you, bundling them together in a handy little tool.
- Check out the tool’s GitHub page and read about some of the available sources. If a source requires an API key, you won’t be able to use it without first creating an account with that service (not necessary for this class).
- Pick some of the sources that look interesting and try them out– see what you can find!
- Make sure you run at least the
subdomaincenter and urlscan sources. What subdomains did you find?
Remember that theHarvester is mostly a passive recon tool. It’s not actively scanning secretcorp.org, but instead just looking at pre-collected data. For example, you should have tried the subdomaincenter source earlier. The website for that source is here.
Subdomain Center scours the web, gathering and interpreting data from from all over the Internet.
This type of passive reconnaissance isn’t really “hacking”– it’s more like reading what’s freely available.
Sometimes these tools are not reliable. As an ethical hacker, it’s imperative not to become overly reliant on any single tool or set of tools for security assessments and penetration testing. Hacking, at its core, is about adopting the methodology and mindset of an attacker, which requires a deep understanding of the underlying principles of cybersecurity, the intricacies of network architectures, and the vulnerabilities that can be exploited. Tools, while invaluable for efficiency and automating certain tasks, can sometimes obscure the broader picture, limiting one’s ability to think creatively and adaptively about potential security threats.
A tool-centric approach may lead to a false sense of security, as these tools can only identify vulnerabilities they are programmed to find, potentially missing novel or complex attack vectors. Additionally, reliance on tools can hinder the development of critical problem-solving skills and the intuitive understanding needed to anticipate and counteract sophisticated cyber threats. Ethical hackers should use tools as aids, not crutches, complementing their technical acumen with a strategic mindset that prioritizes comprehensive security assessments over the convenience of automated scans. This balanced approach, combining deep technical knowledge with a broad strategic perspective, is essential for identifying and mitigating the full spectrum of cybersecurity threats.
Exercise 2: Certificate Transparency
Certificate Transparency (CT) is a security standard and set of protocols that aims to increase transparency and accountability in the digital certificate issuance process. It is designed to make it more difficult for attackers to obtain fraudulent certificates for domain names, and to make it easier to detect and revoke such certificates if they are issued. This is achieved by creating a public, append-only log of all digital certificates issued by a certificate authority (CA), which can be audited by anyone. CT logs are used to verify that a certificate was properly issued by a CA and has not been revoked.
These CT logs are a gold mine for passive reconnaissance and OSINT! There are several websites that provide information and tools related to certificate transparency:
- crt.sh - This website allows you to search for certificates in various CT logs and view the details of each certificate.
- CertSpotter - This website allows you to monitor certificate transparency logs for new certificates issued for a specific domain name.
- CT Logs - This website is operated by Google and provides a list of all CT logs that are currently in operation, as well as information on how to submit certificates to the logs.
- SSLMate - This website provides a list of CT logs that SSLMate supports and also gives the user the ability to monitor the logs.
- CertStream - This website provides a real-time feed of all certificates seen by publicly trusted CT logs.
These are just a few examples of websites that provide information and tools related to certificate transparency.
Go to https://crt.sh and try to find additional hosts in the secretcorp.org domain. Alternatively, you can also use theHarvester to pull crt.sh data by using --source crtsh.
NOTE: Sometimes, crt.sh will not work. Try again later.
Exercise 3: Recon of SecretCorp
Use the tools you just practiced to perform detailed passive reconnaissance of secretcorp.org. Find as many of the following as you can:
- What SecretCorp.org subdomains were you able to find? There should be at least 4 subdomains.
- Were you able to find the web mail portal?
- Based on your findings. Who is the contact person for IT Support?
- Who is the CEO of the company?
- Who is the sales executive?
- What types of products were they selling recently?
- What email addresses were you able to find?
- Did you find any interesting files?
- Were you able to decode the encoded message in one of the pages you found?
- How about their Cloud offer? Did you find information about their customers? What about the hints within their cloud page about other OSINT tools?
- Did you find information about “knock” within the page that has information about SecretCorp’s cloud offer?
Bonus
Using osintframework.com, navigate to Domain Name -> Whois Records. Use one of these tools to investigate the WHOIS records for secretcorp.org. Did you find anything interesting?